Cyber-enabled crime poses significant risks to South Eastern Europe.
In our increasingly digital world, cyber-enabled crime is one of the fastest growing threats to individual citizens and governments. South Eastern Europe’s vulnerability has been demonstrated by highly damaging cyberattacks allegedly orchestrated by hostile states against the governments of both Albania and Montenegro.1 Furthermore, poor awareness, low investment in basic protective measures, high levels of corruption and unemployment all feed into vulnerabilities. If these deficiencies are not addressed coherently both at the national and regional level, then the rapid pace of technological innovation risks leaving malign actors beyond the reach of regional law enforcement.
Modern technologies expand the criminal toolkit
The proliferation of digital devices has brought with it immense advances in connectivity, but on the flipside fertile ground for cybercriminals. Cybercriminals exploit vulnerabilities in digital infrastructure to commit a wide array of crimes, including hacking, identity theft and financial fraud. Vulnerabilities in devices connected through the ‘internet of things’, for example, allow cybercriminals to infiltrate networks, compromise privacy and launch attacks. Machine learning and artificial intelligence are creating powerful new opportunities for criminal minds. Moreover, underground cybercrime forums and dark web marketplaces facilitate the exchange of illicit goods and services, including stolen data, malware and hacking tools.2 This underground economy thrives on anonymity and encryption, making it difficult for law enforcement agencies to track and prosecute cybercriminals effectively.3 The intelligence gathered by the decoding of encrypted messaging app Sky ECC has revealed insights into how criminals operate in this otherwise hidden environment.4
In addition to using technology, cybercriminals in South Eastern Europe exploit human vulnerabilities through social engineering and psychological manipulation. Phishing scams, for instance, deceive unsuspecting individuals into divulging sensitive information or downloading malicious software by impersonating legitimate entities. Moreover, the proliferation of social media platforms provides cybercriminals with unprecedented access to personal information which they leverage to craft targeted attacks.
The rapid evolution of cybercrime poses significant challenges for law enforcement agencies and regulatory frameworks in South Eastern Europe.5 Traditional policing methods are ill-equipped to combat cyber threats effectively, given the borderless nature of the digital realm and the anonymity afforded by encryption technologies. Moreover, the fragmented regulatory landscape across the region hampers efforts to harmonize cybersecurity policies and enact robust legislative measures. As a result, cybercriminals operate with relative impunity, exploiting jurisdictional loopholes and evading prosecution.
The cybercrime landscape in South Eastern Europe
Malicious software (malware) and ransomware attacks are pervasive in the region. Such attacks target individuals, businesses and government institutions,6 often exploiting vulnerabilities in outdated software and operating systems, but also low levels of awareness or professionalism. In 2022 Montenegro reportedly suffered a cyberattack allegedly carried out by a group called Cuba Ransomware.7 Several institutions in North Macedonia were attacked by ransomware, including the Health Insurance Fund in February 2023 and both the Ministry of Agriculture and the Ministry of Education in September 2022.8 Moreover, at the beginning of 2024 the Health Insurance Fund of República Srpska in Bosnia and Herzegovina suffered a ransomware attack,9 taking the Integrated Health Information System offline for 17 days. This system holds the digital health records of all patients in República Srpska, as well as their insurance status.
Phishing and social engineering usually precede malware and ransomware attacks.10 Phishing attacks, aimed at stealing sensitive information such as login credentials and financial data, are common. For example, in 2022 and 2023 an increasing number of Macedonian websites fell victim to hacking, particularly through phishing tactics.11 A Balkan Investigative Reporting Network article notes that attackers often install malicious content on server operating systems, allowing them to compromise websites.12 A case that compromised the email accounts of government and public sector organizations in North Macedonia is of particular significance. Attackers exploited vulnerabilities in mail servers to send phishing emails from compromised official government accounts to government employees and citizens.13 Several government institutions fell victim to these attacks.
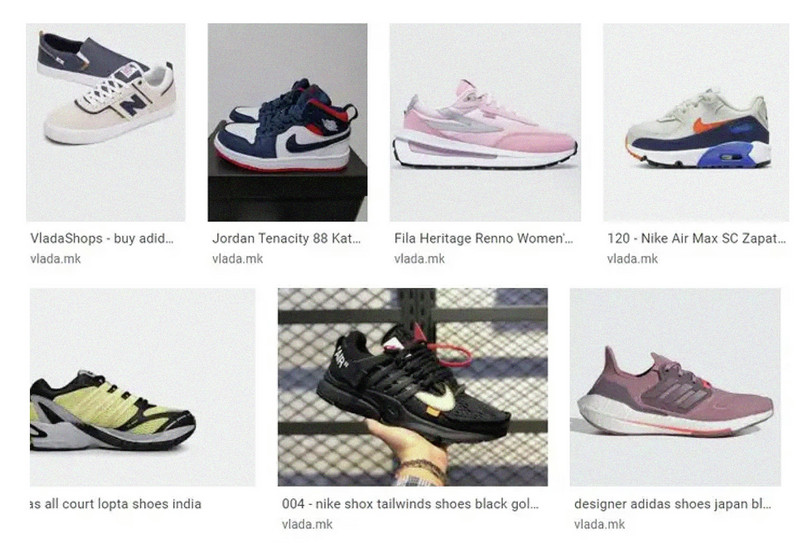
In September 2022, the North Macedonian government’s official website was transformed into a retail webpage where various brands of shoes, bags and other accessories were offered.
Photo: Screengrab reproduced from Vecer
Insider threats pose a significant risk for South Eastern European economies.14 Cybercriminals connect with employees or trusted individuals who in turn knowingly or unwittingly hand over access privileges and facilitate system penetration or the theft of data. For example, in September 2022, the North Macedonian government’s official website was transformed into a retail webpage where various brands of shoes, bags and other accessories were offered,15 possibly due to someone gaining access to the site’s host servers.16 A second government website experienced a similar problem. There has also been a case where an insider mined cryptocurrencies from the North Macedonian Public Procurement Bureau’s website.17
During a severe externally perpetrated cyber crisis that hit Albania in 2022, insider threats played a contributory role in affecting government systems via the internet through the process of exfiltration.18 An attack against Albania’s national database, e-Albania,19 allegedly came through a PDF document sent to the system administrator, who (either knowingly or unwittingly) downloaded the document, which opened a port Remote Desktop Protocol and created free remote access for the hacker. As the administrator had ‘full privilege’, the hacker accessed the whole ‘Enterprise Admin’ of the domain and then deleted all the ‘virtual machines’ (software programmes or servers that run inside the company’s computers).20 This can cause significant disruption and enable theft of data.
A severe external cyberattack in Montenegro was also reportedly facilitated by an insider.21 An investigative journalist reported that malicious software was uploaded from one of the government’s computers.22
Distributed denial of service (DDoS) attacks are another tool in the cybercriminal toolkit. These attacks disrupt online services by overwhelming servers with a flood of traffic, causing downtime and financial losses for businesses. In some cases, the attacks are simply malicious. In others, they can be linked to ransomware: such attackers either demand a ransom to stop the attack or offer ‘protection’ services to prevent future attacks. North Macedonia, Montenegro, Bosnia and Herzegovina, Kosovo, Greece, Slovenia and Serbia have all faced debilitating DDoS attacks between 2022 and 2024.23
Preying on socio-economic vulnerability
Cybercriminals target vulnerable individuals and businesses, taking advantage of economic disparities, unemployment, political instability, cultural diversity, weak cybersecurity infrastructure, and limited awareness and education about cybersecurity.
South Eastern European countries are more vulnerable than their more developed peers in part because cybercriminals suspect these nations have fewer resources to invest in cybersecurity measures. For example, joint research by the UK Cyber Security Excellence Centre and the Balkan Investigative Reporting Network in April 2023 highlighted that Bosnia and Herzegovina lacks adequate computer emergency response teams. This research also cited the prolonged absence of an effective legislative framework as a key problem for the country’s cybersecurity.24 Albania,25 Montenegro,26 North Macedonia, Serbia and Kosovo face similar challenges.27
Another pressing socio-economic challenge that offers an opportunity for cybercrime to flourish is the high unemployment rates across South Eastern European economies, especially among young people. Cybercriminals may exploit this by offering job opportunities that seem legitimate but are actually fronts for illegal activities such as money laundering or distributing malware. For example, a Bosnian and Herzegovinian cybercrime group known as DD4BC was involved in developing software meant to exploit weaknesses in digital Bitcoin wallets for the purpose of theft.28 A young entrepreneur from North Macedonia was identified by Citizen Lab as producing spyware found in the phones of two exiled Egyptians. His company Cytrox was backlisted by the US government, along with its parent company Intellexa.29
On top of this, limited awareness about cybersecurity risks and lack of education about safe online practices make individuals and businesses in South Eastern Europe more vulnerable to cybercrime.30
Law enforcement agencies often lack the resources and expertise to investigate and prosecute cybercriminals adequately.31 Political instability also contributes to inadequate legal frameworks and enforcement mechanisms that hamper efforts to combat cybercrime effectively.
Corruption is a significant issue for cybersecurity in most of South Eastern Europe. For example, an attack on the electoral commission in North Macedonia in 2020 revealed a lack of transparency and procurement practices to safeguard information and communication systems. Cyberattacks in Albania and Montenegro are also likely to have been facilitated by corruption.32 Cybercriminals can avoid detection and prosecution, including by bribing officials to turn a blind eye to their activities.33 Although bilateral donors have invested in human resources development across the region’s economies, poor leadership and the politicization of public administration have resulted in cyber capacity being neglected, exacerbating a brain drain to the private sector or to Western Europe.
The intertwining of socioeconomic factors (particularly corruption), organized crime and cyber threats pose multifaceted challenges to the stability, security and development of South Eastern Europe. The pervasive influence of criminal networks undermines governance structures, fosters distrust in public institutions and hampers economic growth. Moreover, the proliferation of cyber threats exacerbates vulnerabilities in critical infrastructure, compromises data security and poses risks to national security, especially in an era of increasing geopolitical fragmentation.
Cybercrime as a threat to national security
The proliferation of state-sponsored cyber operations and espionage activities in South Eastern Europe has geopolitical implications, exacerbating tensions between neighbouring states and undermining regional stability. The weaponization of cyberspace for political ends heightens the risk of diplomatic friction, conflict escalation and wider threats to national security. Attacks may come from outside the region (including from great powers) or from neighbouring states.
Recent attacks suggest that the region’s countries are ill-prepared, perhaps due to an insufficient understanding of the risks, particularly in terms of how certain types of cybercrime may be linked to cyberattacks that threaten national security. For example, in some cases, cybercriminals – hired to carry out crime-as-a-service – use DDoS attacks as a diversionary tactic to draw the attention of security teams away from other malicious activities, such as data breaches or network infiltration attempts. Cybercriminals acting in the interest of foreign actors may also launch DDoS attacks to assess the resilience of a target’s network infrastructure and identify weaknesses that can be exploited in future attacks or other types of cybercrimes. Such attacks can disrupt essential services, compromise sensitive information, or sow discord within target countries.
Data-rich state security institutions are particularly vulnerable. Attacking these targets enable the attackers to explore grey areas between law enforcement and national security and to gather valuable data to sell on the darknet or to be used as a predicate to other crimes.
According to the US Federal Bureau of Investigation (FBI), in 2021 attackers continuously accessed Albanian government servers to harvest data as a prelude to using ransomware and launching a destructive ‘wiper’ attack that destroyed public data using disk-wiping malware in July 2022.34 Albania’s Prime Minister Edi Rama blamed Iran for the main attack in a televised address in September that year, in common with the analysis of the FBI, US Cybersecurity and Infrastructure Security Agency, the UK National Cyber Security Centre and Microsoft.35 Reportedly, hackers were also able to gather, delete and circulate classified information including the identities of hundreds of undercover Albanian intelligence officers, while also publishing the emails of the director of intelligence, hampering the government’s ability to function.36
The compromised information reportedly included more than 17 years’ worth of data tracking everyone who entered and exited the country from the government’s ‘Total Information Management System’, as well as data from private institutions such as bank customers’ financial records.37 Hackers shut down government websites by using malicious software to encrypt the victims’ data and make it inaccessible, enabling them to blackmail the government and causing a cascade of catastrophic effects for Albanian public services that had ironically originally been digitized to circumvent slow and corrupt bureaucratic public processes.38
A month after the attack against Albania began in earnest, Montenegro was hit in August 2022 by a massive cyberattack allegedly perpetrated by Russia.39 The attack ‘crippled’ state-run transportation services, water and electricity systems, and online platforms for several days.40 The severity of these cyberattacks was described by experts as unprecedented in their intensity and the longest in Montenegro’s history.41
While a strong consensus exists over the origins of these major attacks on both Albania and Montenegro, it is often difficult to confirm attribution. Attackers often use sophisticated techniques to obfuscate their identity, such as spoofing internet protocol addresses, utilizing proxy servers, or employing botnets composed of compromised systems in different geographic locations. Additionally, cyber attackers frequently exploit zero-day vulnerabilities and other sophisticated methods that leave minimal traces.42
In digital forensics, the sheer volume and complexity of data, combined with the potential for anti-forensic techniques such as data encryption or destruction, complicate the process of collecting, preserving and analyzing digital evidence in a manner that is reliable and admissible in court. This complexity is further compounded by the rapid evolution of technology and the legal and jurisdictional challenges associated with cross-border cyber incidents. Moreover, authoritarian regimes utilize proxy actors to act on their behalf, ranging from cybercrime freelancers (hackers for hire) to bespoke enterprises that act in the digital domain when instructed to do so.
That said, governments have developed methods to establish culpability for state-sponsored cyberattacks,43 often by combining technical, behavioural and contextual evidence. Technical analysis includes identifying unique malware signatures, command-and-control infrastructure and attack patterns that are consistent with known state-sponsored groups. Behavioral evidence involves examining the tactics, techniques and procedures (TTPs) that match those previously associated with a particular state’s cyber operations. Contextual evidence includes geopolitical analysis, such as the timing of the attack in relation to international events or the strategic interests of the state under suspicion. Additionally, intelligence gathered from human sources, intercepted communications, or insider information can provide direct or circumstantial evidence linking the attack to a state. Collaboration between governments, cybersecurity firms and international organizations also plays a critical role in corroborating these findings and building a comprehensive case for apportioning responsibility.
Reducing vulnerabilities
A basic preventive measure is to invest in robust cybersecurity infrastructure, including advanced firewalls, intrusion detection systems, encryption protocols and security software to protect critical infrastructure and sensitive data.
Promoting cybersecurity awareness and education initiatives among citizens, businesses and government employees can help in building resilience. Educating users about common cyber threats, best practices for securing their devices and data, and the importance of reporting cyber incidents can significantly reduce the risk of successful cyberattacks.
A stronger legal framework is also vital. Enacting and enforcing comprehensive cybersecurity laws and regulations can provide a legal framework for addressing cybercrime and enhancing national security. These laws should cover areas such as data protection, critical infrastructure protection, and cybercrime investigation and prosecution.
Providing training programmes and capacity-building initiatives for law enforcement agencies, cybersecurity professionals and government officials – often funded by donors – can enhance their capacity to prevent, detect and respond to cyber threats effectively, but they are not a panacea. It is also vital for governments in the region to develop their own robust incident response and crisis management plans to mitigate cyber threats. These plans should outline procedures for detecting, containing and recovering from cyber incidents, as well as mechanisms for coordinating responses across government agencies and stakeholders. Related to this is the need for continuous monitoring mechanisms and threat intelligence capabilities to help organizations identify and respond to emerging cyber threats in real-time. By staying abreast of the latest cyber threats and trends, South Eastern European economies can proactively adapt their cybersecurity measures to mitigate evolving risks.
Because of their transnational nature, addressing cyber threats requires cooperation. This includes public–private partnerships between government agencies and private sector organizations including information sharing, threat intelligence and collaborative responses. Greater regional cooperation is vital. So too is wider international cooperation, extending to regional linkages with Europol, INTERPOL and the United Nations, to share threat intelligence, coordinate cybercrime investigations, and harmonize cybersecurity standards and best practices. Such partnerships can also help the region’s nations keep abreast of developments related to artificial intelligence, machine learning, blockchain and quantum cryptography.
Notes
-
The Global Initiative Against Transnational Organized Crime (GI-TOC)’s Global Organized Crime Index 2023 indicates that the threat posed by cyber-dependent crime in South Eastern Europe is high compared to other parts of the world. Albania, Bulgaria and Romania scored 6.0 out of 10 and Montenegro and North Macedonia 5.50 compared to the global average of 4.55. The higher the score, the worse the performance. ↩
-
Hotspots of organized crime in the Western Balkans: Local vulnerabilities in a regional context, GI-TOC, May 2019. ↩
-
Sheelagh Brady and Metodi Hadji-Janev, Western Balkans security synopsis: Reflections and recommendations from the 8th Regional Security Coordination Conference, Regional Cooperation Council, 13–15 November 2023. ↩
-
Observatory of Illicit Economies in South Eastern Europe, Decryption of messaging app provides valuable insight into criminal activities in the Western Balkans and beyond, Risk Bulletin, Issue 13, GI-TOC, September–October 2022. ↩
-
Western Balkans: Emerging cyber threats, PricewaterhouseCoopers (PwC) Serbia, 2023. ↩
-
Samir Kajosevic, Western Balkans urged to prepare for uptick in cyber-attacks, Balkan Insight, 12 September 2022. ↩
-
Montenegro blames criminal gang for cyber attacks on government, Reuters, 1 September 2022. ↩
-
Miroslava Simonovska, Побарале ли хакерите откуп за да го одблокираат Фондот за здравство, Ковачевски откри каков бил нападот, Sloboden Pečat, 2023; Sasho Spasoski, Министерството за земјоделство еден месец не може да закрепне од рускиот хакерски напад, Meta.mk, 27 October 2022; Министерството за образование под хакерски напад, Faktor, 10 September 2022. ↩
-
Након озбиљног напада криминалних група на ИЗИС предузете све предвиђене мјере, Srna, 5 January 2024; see also Vladimir Kalinski, Рекорден број хакерски напади врз институции, голем дел не пријавуваат, Radio Free Europe/Radio Liberty (RFE/RL), 11 August 2023. ↩
-
From social engineering to ransomware: How hackers outsmart us, ProWriters, 2023. ↩
-
Vladimir Kalinski, Зачестените сајбер напади на државни сајтови го вклучуваат црвениот аларм, RFE/RL, 21 October 2022. ↩
-
Igor Vujic, Battle for Balkan cybersecurity: Threats and implications of biometrics and digital identity, BIRN, 30 June 2023. ↩
-
Министерството за одбрана се соочило со фишинг напад, RFE/RL, 3 May 2024; Srdjan Davitkov, Внимавајте, има активен фишинг напад под маска на македонската Влада, IT.mk, 20 May 2024. ↩
-
Llausha Zenuni, Who is the ‘hitman’ behind cyber attacks in the Western Balkans?, LinkedIn, 24 October 2022. ↩
-
Патики, Ташни се продавале на Vlada.mk – огромен пропуст на владиниот веб сајт, Vecer, 1 October 2022. ↩
-
Vlada.mk ‘препродава’ патики, дресови, ташни и чевли по поволни цени, IT.mk, 28 September 2022. ↩
-
Meri Jordanovska, Од веб-сајтот на Бирото за јавни набавки се копаа криптовалути: Колку се безбедни државните сајтови?, Vistinomer, 21 October 2022. ↩
-
Gavin Denis, Insider threats in Albania: Identifying and mitigating risks to cybersecurity, 11 May 2023. ↩
-
Aleksander Biberaj et al, Cyber attack against e-Albania and its social, economic and strategic effects, Journal of Corporate Governance, Insurance and Risk Management, 9, 2 (2022), 341–347. ↩
-
The cyber attack was an ‘inside job’, Aktuelno, 2 September 2022. ↩
-
FBI juče stigao u Crnu Goru: Sajber napad bio ‘posao iznutra’, Danas, 2 September 2022. ↩
-
With the help and support of the UK’s Cyber Security Excellence Centre, Bosnian authorities identified that the most common form of cyberattacks are DDoS. Azem Kurtic, Bosnia lacks capacity to fight millions of cyber attacks monthly, report warns, Balkan Insight, 14 April 2023. ↩
-
Ibid. ↩
-
Mentor Beqa, Albania must up its game to meet growing cybersecurity challenges, Balkan Insight, 2 March 2023. ↩
-
Samir Kajosevic, Western Balkans urged to prepare for uptick in cyber-attacks, Balkan Insight, 12 September 2022. ↩
-
A recent look towards cybersecurity in the Western Balkans: How can we improve the cybersecurity level in the region?, Metamorphosis, 2023. ↩
-
Igor Spaic, Bosnia and Herzegovina: Crackdown on ‘cyber blackmail’ group, Organized Crime and Corruption Reporting Project, 13 January 2016. ↩
-
Phil Muncaster, US sanctions predator spyware maker Intellexa, InfoSecurity Magazine, 6 March 2024. ↩
-
Ornela Sollaku, AI for good governance and cybersecurity in the Western Balkans: opportunities and challenges, Geneva Centre for Security Sector Governance, 16 October 2023. A 2022 study by PwC, supported by the UK Government, indicates that ‘a general lack of awareness of cyber risks and threats, across all strands of Western Balkan societies, is one of the key obstacles to building more resilient societies in the region’; see PwC and the International and Security Affairs Centre, Cybersecurity Ecosystem Report, March 2022. For information on Greece, see: Unveiling the knowledge gap: Why cybersecurity awareness lags in Greece, Stolsch, 11 August 2023; for Croatia, see Croats falling prey to internet scams: an overview, The Total Croatian News, 11 May 2023; for Bulgaria, see: Bulgarian companies are most often victims of cyber gangs from Nigeria, Bulgarian National Radio, 9 October 2023; and for Slovenia, see: Simon Vrhovec, Igor Bernik and Blaž Markelj, Explaining information-seeking intentions: Insights from a Slovenian social engineering awareness campaign, Computers & Security, 125 (2023). ↩
-
European Fund for the Balkans and Belgrade Centre for Security Policy, Security issues in the Western Balkans, April 2018. ↩
-
Albanian IT staff charged with negligence over cyberattack, Security Week, 1 December 2022; Sajber napad mogao bi biti posao iznutra, PV Informer, 2022. ↩
-
The Director of Information Technology (IT) of Albania’s State Police, Ervin Muço, was placed under ‘house arrest’ after allegedly interfering with the system that records the entry and exit of citizens at border points. He also reportedly had a conflict of interest, since he served as an external adviser to the director of the State Cadaster Agency, which the Law on the State Police does not allow. Ervin Muço was arrested after the establishment of the investigative commission at the request of the opposition, Politiko, 10 April 2024. ↩
-
Daryna Antoniuk, Wiper malware found in analysis of Iran-linked attacks on Albanian institutions, The Record, 8 January 2024. ↩
-
It is also widely believed that the attack was in retaliation for Albania offering sanctuary to members of the Mujahedin-e-Khalq, an opposition group banned in Iran. Ayman Oghanna, How Albania became a target for cyberattacks, Foreign Policy, 25 March 2023; Tom Uren, Why Iran’s attack on Albania cannot go unchecked, Seriously Risky Business News, 15 September 2022. ↩
-
Ibid. ↩
-
Sumeet Wadhwani, Iranian hackers target Albania’s border control system in a tit-for-tat operation, Spiceworks, 13 September 2023. ↩
-
UK Government, UK condemns Iran for reckless cyber attack against Albania, 7 September 2022. ↩
-
Dusan Stojanovic, Montenegro wrestles with massive cyberattack, Russia blamed, Associated Press, 12 September 2022. ↩
-
Julia Dickson and Emily Harding, Russia aims at Montenegro, Center for Strategic and International Studies, 13 February 2024. ↩
-
Dusan Stojanovic, Montenegro wrestles with massive cyberattack, Russia blamed, Associated Press, 12 September 2022. ↩
-
A zero-day vulnerability is a security flaw in software that is unknown to the software’s developer. Because the developer is unaware of the issue, there is no fix or patch available. Attackers can exploit this vulnerability to gain unauthorized access, steal data, or cause other damage before the developer has a chance to address the problem. See Trend Micro, Zero-day vulnerability. ↩
-
The role of digital forensics in cybersecurity incident response, CYFOR blog; for a perceptive early take, see: Mark Reith, Clint Carr and Gregg Gunsch, An examination of digital forensic models, International Journal of Digital Evidence, 1, 3 (2002). ↩
